Rsa Decryption Key Calculator
Posted in HomeBy adminOn 29/11/17Rsa Decryption Key Calculator' title='Rsa Decryption Key Calculator' />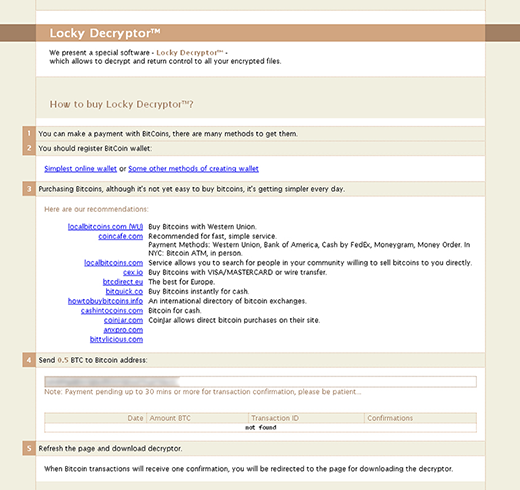 Intel Quartus Prime Pro Edition Handbook Volume 1 Design and Compilation. Introduction to Intel Quartus Prime Pro Edition. Should I Choose the Intel Quartus Prime Pro. No more missed important software updates UpdateStar 11 lets you stay up to date and secure with the software on your computer. Ive got some decryption problems in my Android project. Im getting a string signed with a private key and I have to verifydecrypt it with a public key. Id like. This guide is intended to help with understanding the workings of the RSA Public Key EncryptionDecryption scheme. No provisions are made for high precision. BPTools Cryptographic Calculator first steps. Introduction. The BPTools set consist of applications supporting payment transaction service development. RSA Decryption. Here you can try to bruteforce and decrypt a given RSA message if you have the public key N and e and the message. MlA_ViRW22DESYtWzIWmo_cJNK3KRNyssuXB5wQoE4kOqUucg8RW07E1S_hhpos' alt='Rsa Decryption Key Calculator' title='Rsa Decryption Key Calculator' />RSABack With RSA, initially the person picks two prime numbers. For example p1. Try. In the following you can either manually add your own values, or generate random ones by pressing the button. LectureExamples. Use your own P and Q values Software Tutorial. Next, the n value is calculated. Thus n p x q 1. Next PHI is calculated by PHI p 1q 1 2. Brisa Font more. Secret Key Cryptography. Secret key cryptography methods employ a single key for both encryption and decryption. As shown in Figure 1A, the sender uses the key. Tool to perform RSA computations decrypt. RSA Calculator. Perform RSA computations decrypt. Key Management, Public Key Infrastructure and ID Issuing. I am testing a piece to encrypt and decrypt messages, and I am not 100 on why the algorithm does not seem to work as expected. My test encryption key e 27. My. Md5 Hash Generator. This simple tool computes the MD5 hash of a string. Also available SHA1 hash generator and SHA256 hash generator. The factors of PHI are 1, 2, 4, 5, 1. Next the public exponent e is. PHI is 1 e. is relatively prime with PHI. Thus, the smallest value for e is e 3 The factors of e are 1 and 3, thus 1 is the highest common. Thus n 3. 3 and the e 3 values are the public. The private key d is the inverse of e modulo PHI. Downloadable Explosion Effects Video there. This can be calculated by using extended Euclidian algorithm, to give d7. The encryption and decryption keys are then. As a test you can manually put in p1. The PARTY2 can be given the public keys of e and n, so that PARTY2. PARTY1, using d and n can then. Need For Speed Underground 2 Unlock Everything Pc Mod Minecraft'>Need For Speed Underground 2 Unlock Everything Pc Mod Minecraft. For example, if the message value to decrypt is 4, then. Therefore, the encrypted message c is 3. The encrypted message c is then decrypted by PARTY1 with. Enter the RSA public key or, if known, the RSA private key. An RSA private key. The corresponding public key is. Enciphering. Enter an unenciphered number in the field P. Encipher button. Deciphering. Enter the RSA private key. Enter an enciphered number in the field C and press the.
Intel Quartus Prime Pro Edition Handbook Volume 1 Design and Compilation. Introduction to Intel Quartus Prime Pro Edition. Should I Choose the Intel Quartus Prime Pro. No more missed important software updates UpdateStar 11 lets you stay up to date and secure with the software on your computer. Ive got some decryption problems in my Android project. Im getting a string signed with a private key and I have to verifydecrypt it with a public key. Id like. This guide is intended to help with understanding the workings of the RSA Public Key EncryptionDecryption scheme. No provisions are made for high precision. BPTools Cryptographic Calculator first steps. Introduction. The BPTools set consist of applications supporting payment transaction service development. RSA Decryption. Here you can try to bruteforce and decrypt a given RSA message if you have the public key N and e and the message. MlA_ViRW22DESYtWzIWmo_cJNK3KRNyssuXB5wQoE4kOqUucg8RW07E1S_hhpos' alt='Rsa Decryption Key Calculator' title='Rsa Decryption Key Calculator' />RSABack With RSA, initially the person picks two prime numbers. For example p1. Try. In the following you can either manually add your own values, or generate random ones by pressing the button. LectureExamples. Use your own P and Q values Software Tutorial. Next, the n value is calculated. Thus n p x q 1. Next PHI is calculated by PHI p 1q 1 2. Brisa Font more. Secret Key Cryptography. Secret key cryptography methods employ a single key for both encryption and decryption. As shown in Figure 1A, the sender uses the key. Tool to perform RSA computations decrypt. RSA Calculator. Perform RSA computations decrypt. Key Management, Public Key Infrastructure and ID Issuing. I am testing a piece to encrypt and decrypt messages, and I am not 100 on why the algorithm does not seem to work as expected. My test encryption key e 27. My. Md5 Hash Generator. This simple tool computes the MD5 hash of a string. Also available SHA1 hash generator and SHA256 hash generator. The factors of PHI are 1, 2, 4, 5, 1. Next the public exponent e is. PHI is 1 e. is relatively prime with PHI. Thus, the smallest value for e is e 3 The factors of e are 1 and 3, thus 1 is the highest common. Thus n 3. 3 and the e 3 values are the public. The private key d is the inverse of e modulo PHI. Downloadable Explosion Effects Video there. This can be calculated by using extended Euclidian algorithm, to give d7. The encryption and decryption keys are then. As a test you can manually put in p1. The PARTY2 can be given the public keys of e and n, so that PARTY2. PARTY1, using d and n can then. Need For Speed Underground 2 Unlock Everything Pc Mod Minecraft'>Need For Speed Underground 2 Unlock Everything Pc Mod Minecraft. For example, if the message value to decrypt is 4, then. Therefore, the encrypted message c is 3. The encrypted message c is then decrypted by PARTY1 with. Enter the RSA public key or, if known, the RSA private key. An RSA private key. The corresponding public key is. Enciphering. Enter an unenciphered number in the field P. Encipher button. Deciphering. Enter the RSA private key. Enter an enciphered number in the field C and press the.